Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview
/in Assignment Help, Assignment Help Nursing, BLOG, Homework Help, Nursing Exam Help, Nursing Paper Help, Solved Nursing Essays /by Aimee GraceNursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview
Cerebral aneurysm, a neurological disorder characterized by a weakened area in the blood vessel walls of the brain, presents significant health risks and challenges. This condition involves the formation of an abnormal bulge filled with blood, which can potentially rupture, leading to life-threatening complications such as hemorrhagic strokes. Understanding the causes, symptoms, and treatment options for cerebral aneurysms is crucial for effective management and prevention of adverse outcomes. Despite advancements in medical science, the exact etiology and pathophysiology of cerebral aneurysms remain under extensive research. A comprehensive overview of cerebral aneurysms, including their causes, signs and symptoms, etiology, pathophysiology, DSM-5 diagnosis, treatment regimens, patient education, and concluding remarks can enhance our understanding of this condition and improve strategies for its diagnosis, management, and prevention, ultimately contributing to better patient outcomes and quality of life. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
Causes
Cerebral aneurysms develop due to a combination of genetic predisposition, lifestyle factors, and underlying health conditions. Understanding these causes is essential for identifying individuals at risk and implementing preventive measures.
Genetic Predisposition:
Family history plays a significant role in the development of cerebral aneurysms. Individuals with a first-degree relative, such as a parent or sibling, who has had an aneurysm, are at higher risk. Genetic factors contribute to the structural integrity of blood vessel walls, and inherited conditions like autosomal dominant polycystic kidney disease (ADPKD) and Ehlers-Danlos syndrome can increase susceptibility to aneurysm formation.
Hypertension and Cardiovascular Disease:
High blood pressure is a leading cause of cerebral aneurysms. The constant force of blood against the arterial walls weakens them over time, making them susceptible to bulging and aneurysm formation. Atherosclerosis, a condition characterized by the buildup of plaque in the arteries, can also contribute to aneurysm development by compromising the integrity of blood vessel walls.
Smoking and Alcohol Consumption:
Tobacco use is a significant risk factor for cerebral aneurysms. Smoking damages blood vessels, increasing the likelihood of aneurysm formation and rupture. Similarly, excessive alcohol consumption can elevate blood pressure and weaken blood vessel walls, further predisposing individuals to aneurysms.
Trauma and Injury:
Head trauma, such as a severe blow to the head from a fall or motor vehicle accident, can cause damage to blood vessels in the brain, leading to the formation of aneurysms. Additionally, certain medical procedures or surgeries involving the brain or blood vessels can increase the risk of aneurysm development.
Infections and Inflammatory Conditions:
Infections or inflammatory conditions affecting the blood vessels, such as vasculitis or meningitis, can weaken vessel walls and predispose individuals to cerebral aneurysms. These conditions create an inflammatory response that can damage the structural integrity of blood vessels, increasing the likelihood of aneurysm formation.
In conclusion, cerebral aneurysms develop due to a complex interplay of genetic predisposition, lifestyle factors, and underlying health conditions. Understanding these causes is crucial for identifying at-risk individuals and implementing preventive measures to reduce the incidence and severity of cerebral aneurysms. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
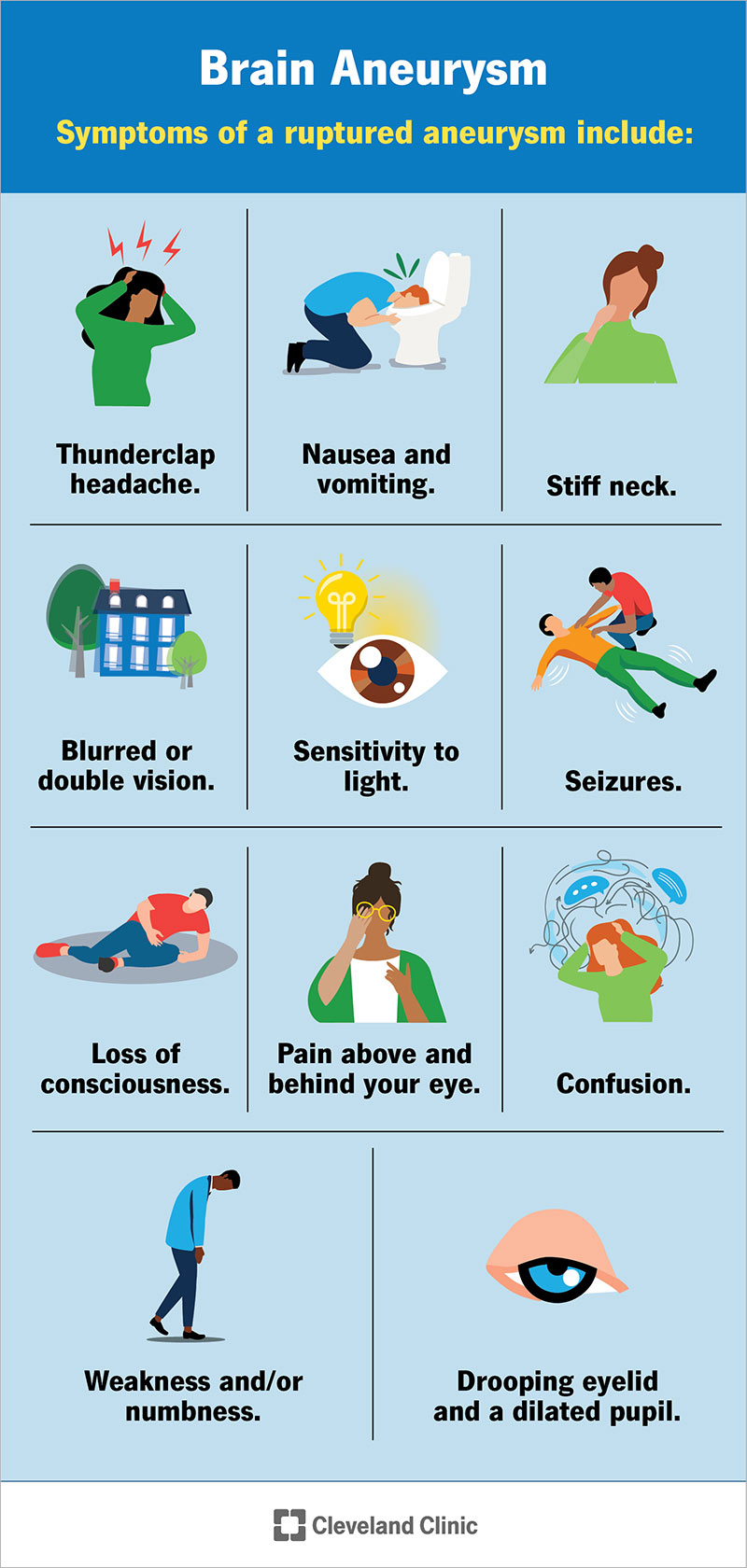
Signs and Symptoms
Recognizing the signs and symptoms of cerebral aneurysms is crucial for early detection and intervention to prevent potentially life-threatening complications. Symptoms can vary depending on the size, location, and rupture status of the aneurysm.
Headache:
One of the most common symptoms of cerebral aneurysms is a severe headache, often described as the worst headache ever experienced. This headache can occur suddenly and may be accompanied by a sharp or stabbing pain, particularly if the aneurysm ruptures.
Nausea and Vomiting:
Individuals with cerebral aneurysms may experience nausea and vomiting, especially when accompanied by a severe headache. These symptoms can result from increased intracranial pressure due to the presence of the aneurysm.
Blurred or Double Vision:
Aneurysms located near the optic nerves or other visual pathways can cause visual disturbances, including blurred or double vision. This occurs as the aneurysm compresses nearby structures in the brain, affecting visual processing.
Sensitivity to Light:
Photophobia, or sensitivity to light, can occur in individuals with cerebral aneurysms, particularly those experiencing severe headaches. Bright lights can exacerbate headache pain and discomfort, leading to sensitivity.
Stiff Neck:
In some cases, individuals with cerebral aneurysms may experience a stiff neck, similar to the symptoms of meningitis. This stiffness can result from irritation of the meninges, and the protective membranes surrounding the brain and spinal cord.
Loss of Consciousness:
A ruptured cerebral aneurysm can lead to a loss of consciousness or fainting, especially if accompanied by a sudden, severe headache. This loss of consciousness is a medical emergency and requires immediate attention.
Seizures:
In rare cases, cerebral aneurysms can cause seizures, particularly if they rupture and lead to bleeding in the brain. Seizures may manifest as convulsions, loss of awareness, or repetitive movements.
Recognizing the signs and symptoms of cerebral aneurysms is crucial for early detection and intervention to prevent potentially life-threatening complications. Individuals experiencing severe headaches, nausea, vomiting, visual disturbances, sensitivity to light, stiff neck, loss of consciousness, or seizures should seek immediate medical attention to rule out the presence of a cerebral aneurysm and receive appropriate treatment. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
Etiology
Understanding the underlying causes and risk factors contributing to the development of cerebral aneurysms is essential for effective prevention and management strategies.

Genetic Factors:
Genetic predisposition plays a significant role in the etiology of cerebral aneurysms. Individuals with a family history of aneurysms are at a higher risk of developing them themselves. Certain genetic disorders, such as autosomal dominant polycystic kidney disease (ADPKD) and Ehlers-Danlos syndrome, are associated with an increased incidence of cerebral aneurysms due to abnormalities in the structure of blood vessel walls.
Hypertension:
High blood pressure is a major risk factor for cerebral aneurysm formation. The constant force of blood against the arterial walls weakens them over time, making them more susceptible to bulging and aneurysm development. Individuals with uncontrolled hypertension are at a significantly higher risk of developing cerebral aneurysms compared to those with normal blood pressure levels.
Smoking and Alcohol Consumption:
Tobacco use and excessive alcohol consumption are modifiable risk factors that contribute to the etiology of cerebral aneurysms. Smoking damages blood vessels and promotes the development of atherosclerosis, increasing the risk of aneurysm formation and rupture. Similarly, alcohol consumption can elevate blood pressure and weaken blood vessel walls, further predisposing individuals to aneurysms.
Age and Gender:
Advancing age is associated with an increased risk of cerebral aneurysm development. Aneurysms are more commonly diagnosed in individuals over the age of 40, with the risk increasing with age. Additionally, women are more likely to develop cerebral aneurysms than men, although the reasons for this gender disparity are not fully understood.
Other Risk Factors:
Other factors that contribute to the etiology of cerebral aneurysms include atherosclerosis, head trauma, certain infections, and inflammatory conditions affecting the blood vessels. These factors can weaken blood vessel walls and increase the likelihood of aneurysm formation, particularly in individuals with preexisting genetic predispositions or underlying health conditions.
The etiology of cerebral aneurysms is multifactorial, involving a complex interplay of genetic predisposition, lifestyle factors, and underlying health conditions. Understanding these contributing factors is essential for identifying at-risk individuals and implementing preventive measures to reduce the incidence and severity of cerebral aneurysms. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
Pathophysiology
The pathophysiology of cerebral aneurysms involves a complex interplay of structural abnormalities within the blood vessel walls, leading to the formation and potential rupture of aneurysms.
Structural Weakness:
Cerebral aneurysms develop due to weaknesses in the arterial wall of the brain’s blood vessels. These weaknesses can be congenital or acquired and are often located at branching points where blood vessels bifurcate. The structural weakness can result from genetic predispositions, underlying health conditions, or environmental factors.
Hemodynamic Stress:
Hemodynamic stress, including factors such as blood flow dynamics and pressure changes within the blood vessels, plays a significant role in the pathophysiology of cerebral aneurysms. Abnormal blood flow patterns, such as turbulent flow or flow diversion, can exert mechanical stress on the weakened arterial wall, contributing to the development and progression of aneurysms.
Aneurysm Formation:
As blood flows through the weakened area of the arterial wall, it exerts pressure, causing the vessel wall to bulge outward and form an aneurysm. The aneurysm typically appears as a small sac or balloon-like protrusion filled with blood, which may continue to grow over time.
Rupture Risk:
The risk of rupture is a critical aspect of the pathophysiology of cerebral aneurysms. Rupture occurs when the pressure within the aneurysm exceeds the strength of the arterial wall, leading to a sudden release of blood into the surrounding brain tissue. Ruptured cerebral aneurysms can cause hemorrhagic strokes, subarachnoid hemorrhage, or other serious neurological complications.
Secondary Complications:
In addition to the immediate risk of rupture, cerebral aneurysms can lead to secondary complications, including thrombosis, inflammation, and compression of surrounding brain structures. Thrombosis within the aneurysm sac can occlude blood flow, leading to ischemia and tissue damage. Inflammation in response to the presence of the aneurysm can further weaken the arterial wall and increase the risk of rupture.
The pathophysiology of cerebral aneurysm involves structural weaknesses within the arterial wall, hemodynamic stressors, aneurysm formation, and the risk of rupture and secondary complications. Understanding these underlying mechanisms is essential for developing effective strategies for the diagnosis, management, and prevention of cerebral aneurysms, ultimately improving patient outcomes and reducing the risk of adverse neurological events. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
DSM-5 Diagnosis
The Diagnostic and Statistical Manual of Mental Disorders, Fifth Edition (DSM-5), does not provide specific diagnostic criteria for cerebral aneurysm, as it primarily focuses on psychiatric and mental health disorders. However, cerebral aneurysm diagnosis is typically made based on clinical presentation, imaging studies, and medical history rather than relying on DSM-5 criteria.
Clinical Presentation:
Individuals with cerebral aneurysms may present with a range of symptoms, including severe headaches, nausea, vomiting, visual disturbances, sensitivity to light, stiff neck, loss of consciousness, or seizures. The sudden onset of a severe headache, often described as the worst headache ever experienced, is a hallmark symptom of a ruptured cerebral aneurysm and requires immediate medical attention.
Imaging Studies:
Diagnostic imaging plays a crucial role in confirming the presence of a cerebral aneurysm and determining its size, location, and potential risks. Common imaging modalities used for diagnosis include computed tomography angiography (CTA), magnetic resonance angiography (MRA), and digital subtraction angiography (DSA). These imaging studies allow healthcare providers to visualize the blood vessels in the brain and identify any abnormalities, such as aneurysms or blood vessel malformations.
Medical History and Risk Factors:
A thorough medical history is essential for diagnosing cerebral aneurysms, as certain risk factors, such as a family history of aneurysms, hypertension, smoking, or a history of head trauma, can increase the likelihood of aneurysm formation. Healthcare providers will also inquire about any previous neurological symptoms or related medical conditions that may be indicative of an underlying aneurysm.
While the DSM-5 does not provide specific diagnostic criteria for cerebral aneurysms, diagnosis is typically based on clinical presentation, imaging studies, and medical history. Prompt recognition and appropriate diagnostic evaluation are crucial for identifying cerebral aneurysms and implementing timely interventions to prevent potentially life-threatening complications such as hemorrhagic strokes or subarachnoid hemorrhage. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
Treatment Regimens
Effective management of cerebral aneurysms involves a combination of medical interventions, surgical procedures, and patient education to minimize the risk of complications and improve outcomes.
Medical Management
Patients with unruptured cerebral aneurysms may undergo medical management to control risk factors and prevent aneurysm growth or rupture. This may include medications to manage hypertension and lifestyle modifications such as smoking cessation and dietary changes to promote cardiovascular health. Regular monitoring through imaging studies is essential to assess aneurysm stability and determine the need for further intervention.
Surgical Intervention:
For individuals with symptomatic or high-risk cerebral aneurysms, surgical intervention may be necessary to prevent rupture and associated complications. Two primary surgical techniques are commonly employed:
- Clipping: Involves surgically placing a metal clip at the base of the aneurysm to isolate it from the circulation and prevent further enlargement or rupture.
- Coiling: Involves inserting a small coil or mesh device into the aneurysm through a catheter, causing the blood to clot within the aneurysm and sealing it off from circulation.
The choice of surgical technique depends on factors such as the aneurysm’s size, location, and the patient’s overall health status. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
Patient Education
Patient education plays a crucial role in the management of cerebral aneurysms, empowering individuals to make informed decisions about their health and adhere to treatment regimens. Key components of patient education include:
- Understanding the Condition: Patients should receive comprehensive information about cerebral aneurysms, including their causes, symptoms, and potential complications. Clear explanations of diagnostic procedures and treatment options help patients feel more engaged in their care.
- Lifestyle Modifications: Educating patients about lifestyle modifications, such as smoking cessation, maintaining a healthy diet, managing stress, and regular exercise, is essential for reducing risk factors associated with cerebral aneurysms and promoting overall cardiovascular health.
- Medication Management: Patients prescribed medications to manage hypertension or prevent blood clotting should receive detailed instructions on medication dosing, potential side effects, and the importance of medication adherence.
- Monitoring and Follow-Up: Patients should understand the importance of regular monitoring through imaging studies to assess aneurysm stability and detect any changes that may require intervention. Encouraging patients to attend scheduled follow-up appointments ensures ongoing evaluation and management of their condition.
- Recognizing Warning Signs: Patients should be educated about the signs and symptoms of aneurysm rupture, such as severe headaches, nausea, vomiting, or changes in consciousness, and instructed to seek immediate medical attention if these symptoms occur.
Effective management of cerebral aneurysms involves a combination of medical interventions, surgical procedures, and patient education. Empowering patients with knowledge about their condition, treatment options, and lifestyle modifications enables them to actively participate in their care and optimize outcomes while reducing the risk of complications associated with cerebral aneurysms. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)
Conclusion
Cerebral aneurysm is a complex neurological disorder characterized by weaknesses in the blood vessel walls of the brain, posing serious risks of rupture and potentially life-threatening complications. This essay has explored various aspects of cerebral aneurysms, including their causes, signs and symptoms, etiology, pathophysiology, DSM-5 diagnosis, treatment regimens, and patient education. By understanding the underlying factors contributing to cerebral aneurysms, implementing effective treatment regimens, and providing comprehensive patient education, healthcare professionals can improve outcomes and reduce the risk of complications associated with this condition. Continued research and public education efforts are essential for enhancing our understanding of cerebral aneurysms and developing innovative strategies for their diagnosis, management, and prevention, ultimately improving patient outcomes and quality of life. (Nursing Paper Example on Cerebral Aneurysm: A Comprehensive Overview)








:max_bytes(150000):strip_icc()/rehabilitation-therapies-for-multiple-sclerosis-4072854-e72137c8397a4d909ce759135c9fa3a8.png)