Nursing Homework Help Example on Understanding and Managing Coeliac Disease: A Comprehensive Approach
Nursing Homework Help Example on Understanding and Managing Coeliac Disease: A Comprehensive Approach
Causes
Coeliac disease is primarily caused by the body’s abnormal response to gluten, a protein found in wheat, barley, and rye. When individuals with coeliac disease consume gluten, their immune system mistakenly identifies it as a threat and launches an immune response against it. This response leads to inflammation and damage to the lining of the small intestine, specifically targeting the villi, finger-like projections responsible for absorbing nutrients.
Genetic predisposition also plays a significant role in the development of coeliac disease. Specific genetic markers, such as the HLA-DQ2 and HLA-DQ8 genes, are strongly associated with an increased risk of developing the condition. Individuals carrying these genetic markers have a higher likelihood of developing an abnormal immune response to gluten.
In addition to genetic factors, environmental triggers contribute to the onset of coeliac disease. One notable environmental factor is the timing of gluten introduction during infancy. Studies suggest that early exposure to gluten, particularly before the age of four months, may increase the risk of developing coeliac disease in genetically susceptible individuals.
Furthermore, factors such as gastrointestinal infections, stress, and pregnancy have been implicated as potential triggers for the onset of coeliac disease. Gastrointestinal infections, in particular, can disrupt the delicate balance of the gut microbiota and trigger immune responses that contribute to the development of autoimmune disorders like coeliac disease.
The interplay between genetic predisposition and environmental triggers underscores the multifactorial nature of coeliac disease. While genetic susceptibility lays the foundation for the condition, environmental factors act as catalysts that trigger the autoimmune response to gluten.
It is important to note that coeliac disease differs from wheat allergy and non-coeliac gluten sensitivity. While these conditions also involve adverse reactions to gluten, they have distinct underlying mechanisms and diagnostic criteria. Coeliac disease specifically involves autoimmune-mediated damage to the small intestine, whereas wheat allergy is an immune response to wheat proteins unrelated to autoimmunity, and non-coeliac gluten sensitivity is characterized by gastrointestinal symptoms without the autoimmune component seen in coeliac disease.
Overall, the causes of coeliac disease are multifaceted, involving a complex interplay of genetic predisposition, environmental triggers, and immune dysregulation. Understanding these underlying causes is essential for effectively managing and treating this chronic autoimmune disorder. (Nursing Homework Help Example on Understanding and Managing Coeliac Disease: A Comprehensive Approach)
Signs and Symptoms
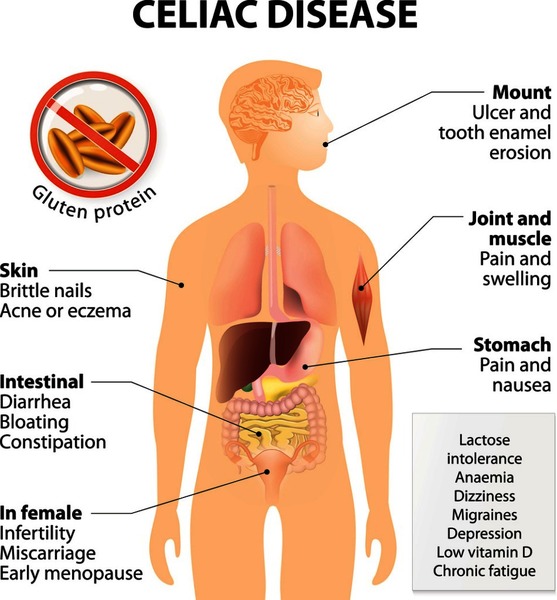
Coeliac disease manifests with a diverse array of signs and symptoms, which can vary widely among affected individuals. These symptoms primarily stem from the immune-mediated damage to the small intestine triggered by gluten ingestion. Understanding these manifestations is crucial for timely diagnosis and management of the condition.
Abdominal Pain and Bloating: Abdominal pain and bloating are common symptoms experienced by individuals with coeliac disease. The inflammation and damage to the lining of the small intestine disrupt normal digestive processes, leading to discomfort and distension in the abdominal region. This symptomatology can range from mild discomfort to severe pain, significantly impacting an individual’s quality of life.
Diarrhea and Constipation: Diarrhea and constipation are hallmark gastrointestinal symptoms of coeliac disease. The inflammation and damage to the intestinal villi impair the absorption of nutrients and water, leading to alterations in bowel habits. While some individuals experience frequent loose stools characteristic of diarrhea, others may present with infrequent or difficult-to-pass stools indicative of constipation.
Fatigue and Weight Loss: Fatigue and unexplained weight loss are common systemic manifestations of coeliac disease. Malabsorption of essential nutrients, including carbohydrates, fats, proteins, vitamins, and minerals, can result in energy depletion and unintentional weight loss despite adequate food intake. This fatigue and weight loss may persist despite efforts to increase caloric intake, highlighting the underlying metabolic disturbances associated with the condition.
Dermatitis Herpetiformis: Dermatitis herpetiformis, a chronic skin rash characterized by intensely itchy and blistering lesions, is a unique extraintestinal manifestation of coeliac disease. This autoimmune skin condition shares a common pathogenesis with coeliac disease, with both conditions triggered by gluten ingestion. Dermatitis herpetiformis predominantly affects the elbows, knees, buttocks, and scalp, although lesions can appear on other body areas as well.
Other Symptoms: In addition to the aforementioned symptoms, individuals with coeliac disease may experience a wide range of other manifestations, including nausea, vomiting, joint pain, headaches, and anemia. These symptoms can vary in severity and may fluctuate over time, making the diagnosis of coeliac disease challenging in some cases.
Overall, the signs and symptoms of coeliac disease encompass a broad spectrum of gastrointestinal and systemic manifestations. Recognition of these diverse presentations is essential for early detection, diagnosis, and initiation of appropriate management strategies aimed at improving patients’ overall health and well-being. (Nursing Homework Help Example on Understanding and Managing Coeliac Disease: A Comprehensive Approach)
Etiology
Coeliac disease is a multifactorial disorder with a complex etiology involving genetic, environmental, and immunological factors. Understanding the underlying mechanisms contributing to the development of coeliac disease is crucial for elucidating its pathogenesis and informing strategies for diagnosis and management.
Genetic Predisposition: One of the key factors contributing to the etiology of coeliac disease is genetic predisposition. Specific genetic markers, particularly the human leukocyte antigen (HLA) genes, play a central role in determining an individual’s susceptibility to the condition. The majority of individuals with coeliac disease carry either the HLA-DQ2 or HLA-DQ8 genotype, which increases their risk of developing an abnormal immune response to gluten.
Environmental Triggers: While genetic predisposition sets the stage for coeliac disease, environmental factors act as triggers that initiate and exacerbate the autoimmune response to gluten. The most well-established environmental trigger is the ingestion of gluten-containing grains, including wheat, barley, and rye. Gluten acts as an antigen that activates the immune system in genetically susceptible individuals, leading to inflammation and damage to the intestinal mucosa.
Early Gluten Exposure: The timing of gluten introduction during infancy has emerged as a significant environmental factor influencing the development of coeliac disease. Studies suggest that early exposure to gluten, particularly before the age of four months, may increase the risk of developing coeliac disease in genetically susceptible individuals. Delaying the introduction of gluten until after six months of age has been associated with a reduced risk of developing the condition.
Microbiota Dysbiosis: Alterations in the gut microbiota, known as dysbiosis, have also been implicated in the etiology of coeliac disease. Disruptions in the composition and function of the gut microbiome can influence immune regulation and intestinal barrier function, predisposing individuals to autoimmune disorders like coeliac disease. Factors such as antibiotic use, gastrointestinal infections, and dietary changes can contribute to microbiota dysbiosis and exacerbate immune-mediated intestinal damage.
Immunological Dysregulation: Immunological dysregulation plays a central role in the pathogenesis of coeliac disease. In genetically susceptible individuals, the ingestion of gluten triggers an abnormal immune response characterized by the production of autoantibodies, including anti-tissue transglutaminase (anti-tTG) and anti-endomysial antibodies (EMA). These antibodies target the intestinal mucosa, leading to inflammation, villous atrophy, and malabsorption of nutrients.
The etiology of coeliac disease is complex and multifaceted, involving a combination of genetic predisposition, environmental triggers, microbiota dysbiosis, and immunological dysregulation. Genetic susceptibility conferred by HLA genes, combined with environmental factors such as early gluten exposure and microbiota dysbiosis, contributes to the initiation and progression of the autoimmune response to gluten. Understanding these underlying mechanisms is essential for developing targeted interventions aimed at preventing, diagnosing, and managing coeliac disease effectively.
Pathophysiology
The pathophysiology of coeliac disease involves a complex interplay of immune-mediated mechanisms that result in inflammation and damage to the small intestine, specifically targeting the villi. Understanding the underlying pathophysiological processes is crucial for elucidating the mechanisms driving the clinical manifestations of the disease and guiding therapeutic interventions.
Immune Response to Gluten: The primary trigger for the pathophysiology of coeliac disease is the ingestion of gluten, a protein found in wheat, barley, and rye. In genetically susceptible individuals carrying HLA-DQ2 or HLA-DQ8 alleles, gluten acts as an antigen that triggers an abnormal immune response. This response involves the activation of T lymphocytes and the production of proinflammatory cytokines, leading to localized inflammation within the intestinal mucosa.
Intestinal Villous Atrophy: One of the hallmark features of coeliac disease is villous atrophy, characterized by the flattening and loss of the finger-like projections known as villi that line the small intestine. The inflammatory response triggered by gluten ingestion results in damage to the intestinal epithelium, leading to villous atrophy and a decrease in the absorptive surface area of the intestine. This villous atrophy impairs the absorption of nutrients, leading to malabsorption and subsequent systemic manifestations of the disease.
Increased Intestinal Permeability: In addition to villous atrophy, coeliac disease is associated with increased intestinal permeability, also known as “leaky gut.” Disruption of the intestinal barrier function allows for the translocation of luminal antigens, including gluten peptides, across the intestinal epithelium into the lamina propria. This breach in intestinal integrity exacerbates the immune response, perpetuating inflammation and tissue damage within the small intestine.
Autoantibody Production: The immune response to gluten in coeliac disease is characterized by the production of autoantibodies targeting specific tissue antigens. Anti-tissue transglutaminase (anti-tTG) and anti-endomysial antibodies (EMA) are two well-characterized autoantibodies that are commonly elevated in individuals with coeliac disease. These autoantibodies contribute to the immune-mediated destruction of intestinal tissue and are used as diagnostic markers for the disease.
Systemic Manifestations: Beyond the gastrointestinal tract, coeliac disease can have systemic manifestations resulting from the malabsorption of nutrients and the systemic immune response. These manifestations may include nutritional deficiencies, osteoporosis, dermatitis herpetiformis, neurological disorders, and reproductive issues. The systemic effects of coeliac disease underscore the importance of early detection and comprehensive management to prevent long-term complications.
In summary, the pathophysiology of coeliac disease involves an immune-mediated cascade triggered by gluten ingestion, leading to inflammation, villous atrophy, increased intestinal permeability, autoantibody production, and systemic manifestations. Understanding these underlying processes is essential for guiding diagnostic and therapeutic strategies aimed at managing the disease and improving patient outcomes.
DMS-5 Diagnosis
The Diagnostic and Statistical Manual of Mental Disorders, Fifth Edition (DSM-5), provides criteria for the diagnosis of various medical conditions, including coeliac disease. While DSM-5 primarily focuses on psychiatric disorders, it includes specific guidelines for diagnosing coeliac disease based on clinical presentation, serologic testing, and histological examination of small intestinal biopsies.
Clinical Presentation: The DSM-5 criteria for diagnosing coeliac disease emphasize the importance of recognizing the characteristic clinical features associated with the condition. Individuals suspected of having coeliac disease typically present with a combination of gastrointestinal symptoms, such as abdominal pain, bloating, diarrhea, constipation, and weight loss. Additionally, extraintestinal manifestations, including dermatitis herpetiformis, anemia, fatigue, and osteoporosis, may also be present.
Serologic Testing: In addition to clinical evaluation, serologic testing plays a crucial role in the DSM-5 diagnosis of coeliac disease. Blood tests measuring specific antibodies associated with the condition, such as anti-tissue transglutaminase (anti-tTG) and anti-endomysial antibodies (EMA), are commonly used to screen for coeliac disease. Elevated levels of these antibodies indicate an abnormal immune response to gluten and support the diagnosis of coeliac disease.
Histological Examination: The definitive diagnosis of coeliac disease is confirmed through histological examination of small intestinal biopsies obtained via upper gastrointestinal endoscopy. The DSM-5 criteria specify the presence of characteristic histopathological findings consistent with coeliac disease, including villous atrophy, crypt hyperplasia, and intraepithelial lymphocytosis, in the small intestinal mucosa. These histological changes are indicative of immune-mediated damage to the intestinal epithelium triggered by gluten ingestion.
Response to Gluten-Free Diet: Furthermore, the DSM-5 criteria acknowledge the importance of assessing the response to a gluten-free diet as part of the diagnostic process for coeliac disease. Improvement or resolution of symptoms, normalization of serologic markers, and restoration of small intestinal histology following adherence to a strict gluten-free diet provide additional supportive evidence for the diagnosis of coeliac disease.
Differential Diagnosis: Finally, the DSM-5 emphasizes the need to consider and exclude other conditions with overlapping clinical features in the differential diagnosis of coeliac disease. Conditions such as wheat allergy, non-coeliac gluten sensitivity, inflammatory bowel disease, and irritable bowel syndrome may present with similar gastrointestinal symptoms but have distinct underlying mechanisms and diagnostic criteria.
In summary, the DSM-5 provides comprehensive guidelines for diagnosing coeliac disease based on clinical presentation, serologic testing, histological examination, and response to treatment. By integrating these criteria, healthcare professionals can accurately identify and manage individuals with coeliac disease, facilitating timely intervention and improved patient outcomes. (Nursing Homework Help Example on Understanding and Managing Coeliac Disease: A Comprehensive Approach)
Treatment Regimens and Patient Education:
Managing coeliac disease requires a comprehensive treatment regimen centered around strict adherence to a gluten-free diet and ongoing patient education. The primary goals of treatment are to alleviate symptoms, promote intestinal healing, prevent long-term complications, and improve overall quality of life for individuals with coeliac disease.
Gluten-Free Diet: The cornerstone of treatment for coeliac disease is the adoption of a strict gluten-free diet. This involves completely eliminating all sources of gluten from the diet, including wheat, barley, rye, and their derivatives. Patients must carefully read food labels, as gluten can be found in various processed foods, condiments, and medications. Additionally, cross-contamination with gluten-containing products must be avoided in food preparation and cooking.
Dietary Guidance: Patients with coeliac disease benefit from guidance provided by registered dietitians or healthcare professionals with expertise in managing gluten-free diets. These professionals can help patients navigate food choices, identify gluten-free alternatives, plan balanced meals, and ensure adequate nutrient intake despite dietary restrictions. Dietary counseling may also address strategies for dining out, traveling, and managing social situations involving food.
Nutritional Supplementation: In some cases, individuals with coeliac disease may require nutritional supplementation to address deficiencies resulting from malabsorption of nutrients. Common deficiencies observed in coeliac disease include iron, calcium, vitamin D, vitamin B12, and folate. Supplementation with vitamins and minerals may be prescribed based on individual nutritional needs and laboratory assessments.
Monitoring and Follow-Up: Regular monitoring and follow-up with healthcare providers are essential components of coeliac disease management. This includes periodic assessment of symptoms, serologic markers, and nutritional status to ensure adequate disease control and compliance with the gluten-free diet. Follow-up evaluations may also include repeat small intestinal biopsies to assess mucosal healing in select cases.
Patient Education: Patient education plays a crucial role in empowering individuals with coeliac disease to effectively manage their condition and make informed lifestyle choices. Key aspects of patient education include:
- Understanding Coeliac Disease: Educating patients about the underlying pathophysiology, clinical manifestations, and long-term implications of coeliac disease enhances their awareness and engagement in self-management strategies.
- Gluten-Free Diet Education: Providing comprehensive education on adopting and maintaining a gluten-free diet is essential for successful disease management. Patients should be educated about reading food labels, identifying hidden sources of gluten, and navigating social situations involving food.
- Symptom Management: Educating patients about strategies for managing gastrointestinal symptoms, such as abdominal pain, bloating, and diarrhea, improves their ability to cope with symptom flare-ups and enhances their quality of life.
- Nutritional Guidance: Offering guidance on obtaining adequate nutrition while adhering to a gluten-free diet is crucial for preventing nutritional deficiencies and optimizing overall health. Patients should be educated about gluten-free sources of essential nutrients and the importance of nutritional supplementation when necessary.
- Lifestyle Modifications: Discussing lifestyle modifications, such as stress management techniques, regular physical activity, and smoking cessation, can help support overall health and well-being in individuals with coeliac disease.
- Monitoring and Follow-Up: Emphasizing the importance of regular monitoring, follow-up appointments, and communication with healthcare providers facilitates ongoing disease management and early intervention for any emerging issues or concerns.
The treatment regimen for coeliac disease encompasses strict adherence to a gluten-free diet, nutritional supplementation as needed, regular monitoring, and ongoing patient education. Empowering individuals with coeliac disease with the knowledge and skills to effectively manage their condition promotes optimal health outcomes and enhances their quality of life. By incorporating these components into a comprehensive treatment approach, healthcare providers can support patients in successfully navigating the challenges of living with coeliac disease.




